Category: Cyber space challenges
Ransomware
01, Dec 2022

Context:
- The services at the AIIMS in the national capital were affected for the 7th consecutive day, after the hospital’s server was subjected to a ransomware attack.
What are Cyber Attacks?
- It is a malicious and deliberate attempt by an individual or organization to breach the information system of another individual or organization.
- There are various types of cyberattacks like malware, phishing, denial of service attacks, etc.
Different types of Malware:
- Malware is the shortened form of malicious software. It is the general term for any program that is designed to damage, disrupt, or hack a device. Malware includes viruses, Ransomware, spyware, Trojan, adware, etc.
- Viruses are malicious pieces of code that infect your device without your knowledge. They can affect your device’s performance, delete files, send spam, and even corrupt your hard drive. They multiply and spread to other machines, often before you’re aware of an infection.
- Ransomware is malicious programs that block access to your device until you pay a ransom fee to its creator. It is often very difficult and expensive to remove.
- Spyware is software that spies on you, tracking your internet activities in order to send advertising (Adware) back to your system.
- Worm is a program that replicates itself and destroys data and files on the computer. Worms work to “eat” the system operating files and data files until the drive is empty.
- Trojan is a type of malware that are written with the purpose of discovering your financial information, taking over your computer’s system resources, and in larger systems creating a “denial-of-service attack” which is making a machine or network resource unavailable to those attempting to reach it. Example: Google, AOL, Yahoo or your business network becoming unavailable.
- Phishing is a cybercrime in which a target or targets are contacted by email, telephone, or text message. This is done by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords.
Steps taken by the Government to spread awareness about cyber-crimes:
- Online cybercrime reporting portal has been launched to enable complainants to report complaints pertaining to Child Pornography/Child Sexual Abuse Material, rape/gang rape imageries or sexually explicit content.
- A scheme for establishment of Indian Cyber Crime Coordination Centre (I4C) has been established to handle issues related to cybercrime in the country in a comprehensive and coordinated manner.
- Establishment of National Critical Information Infrastructure Protection Centre (NCIIPC) for protection of critical information infrastructure in the country.
- All organizations providing digital services have been mandated to report cyber security incidents to CERT-In expeditiously.Cyber Swachhta Kendra (Botnet Cleaning and Malware Analysis Centre) has been launched for providing detection of malicious programmes and free tools to remove such programmes.
- Formulation of Crisis Management Plan for countering cyber-attacks and cyber terrorism.
ZOOM NOT A SAFE PLATFORM, SAYS MHA
18, Apr 2020

Why in News?
- Recently, the Ministry of Home Affairs (MHA) has issued an advisory that Zoom video conference is not a safe platform.
What is the Issue?
- Zoom has seen an exponential rise in usage in India as office-goers remain at home due to the lockdown, imposed to curb the Covid-19 pandemic.
- Over 90,000 schools across 20 countries have started using it regularly.
- The maximum number of daily meeting participants of approximately 10 million at the end of December 2019 grew to more than 200 million daily meeting participants in March.
- It has been used extensively by everyone including the central and state ministers for official purposes and Conducting Meetings.
About Zoom:
- Zoom is a US-based video communication and videoconferencing platform.
- This Silicon Valley-based company appears to own three companies in China through which at least 700 employees were paid to develop Zoom’s software.
- This arrangement is apparently an effort at labour arbitrage in which Zoom can avoid paying US wages while selling to US customers, thus increasing their profit margin.
- However, this arrangement may make Zoom responsive to pressure from Chinese authorities.
- Reportedly, few calls made through the app are routed through servers in China.
Cautions made by CERT-IN:
- Earlier, the Computer Emergency Response Team, India (CERT-In) had also issued advisories cautioning on the use of Zoom for office meetings.
- CERT-IN is an organisation of the Ministry of Electronics and Information Technology, Government of India, with the objective of securing Indian cyberspace.
- It collects, analyses and disseminates information on cyber incidents, and also issues alerts on cyber security incidents.
- CERT-IN provides Incident Prevention and Response Services as well as Security Quality Management Services.
- It warned that the insecure usage of the platform may allow cyber criminals to access sensitive information such as meeting details and conversations giving rise to cyber frauds.
- It also highlighted multiple vulnerabilities which could allow an attacker to gain elevated privileges or obtain sensitive information.
Why Zoom is Not Safe?
- Citizen Lab, based at the University of Toronto, found significant weakness in Zoom’s encryption that protects meetings.
- It identified the transmission of meeting encryption keys through China.
- The lab has raised two primary concerns- geo-fencing and Meeting Encryption.
- Geo-fencing is a location-based service in which an app or other software uses GPS, RFID, Wi-Fi or cellular data to trigger a pre-programmed action when a mobile device or RFID tag enters or exits a virtual boundary set up around a geographical location, known as a geo-fence.
What is the Response from Zoom?
- Zoom Founder and CEO Eric S Yuan has apologised and assured the people that the privacy and security expectations would be taken care of.
- Zoom has added additional features such as placing a new security icon in the meeting controls, changing Zoom’s default settings and enhancing meeting password complexity, among others.
- It has also added that soon, account admins will have the ability to choose whether or not their data is routed through specific Data Center Regions.
Suggestions given by the Ministry:
- The users are suggested to set strong passwords and enable “waiting room” features so that call managers could have better control over the participants.
- Users should also avoid using personal meeting ID to host events and instead use randomly generated meeting IDs for each event.
- People using the app should not share meeting links on Public platforms.
Who deals with Cyber-crime Issues in India?
- Indian Cyber Crime Coordination Centre (I4C):
- The scheme to set up I4C was approved in October 2018, to deal with all types of cybercrimes in a comprehensive and coordinated manner.
- It has Seven Components:
- 1.National Cyber Crime Threat Analytics Unit
- 2.National Cyber Crime Reporting Portal
- 3.National Cyber Crime Training Centre
- 4.Cyber Crime Ecosystem Management Unit
- 5.National Cyber Crime Research and Innovation Centre
- 6.Cyber Crime Forensic Laboratory Ecosystem
- .7Platform for Joint Cyber Crime Investigation Team.
- Various States and Union Territories (UTs) have consented to set up Regional Cyber Crime Coordination Centres.
- This state-of-the-art Centre is located in New Delhi.
CYBER-ATTACKS ON HEALTH CARE INSTITUTIONS
09, Apr 2020

Why in News?
- The International Criminal Police Organisation (Interpol) has warned member countries that cybercriminals are attempting to target major hospitals and other institutions on the front lines of the fight against COVID-19 with ransomware.
About International Criminal Police Organization (INTERPOL):
- Interpol is an intergovernmental organization that helps coordinate the police force of 194 member countries.
- Each of the member countries hosts an Interpol National Central Bureau (NCB). This connects their national law enforcement with other countries and with the General Secretariat.
- The Central Bureau of Investigation (CBI) is designated as the National Central Bureau of India.
- The General Secretariat provides a range of expertise and services to the member countries.
- It is headquartered in Lyon, France
- Interpol Notices are international requests for cooperation or alerts allowing police in member countries to share critic.

Key Points:
- In an alert sent to 194 nations, including India, Interpol said that the hospitals and institutions had become targets of ransomware attacks.
- Interpol’s Cybercrime Threat Response Team had detected an increase in the number of attempted ransomware attacks against key organisations and infrastructure engaged in the virus response.
- Cybercriminals are using ransomware to hold hospitals and medical services digitally hostage, preventing them from accessing vital files and systems until a ransom is paid.
- The attacks were designed to lock these institutions out of their critical systems in an attempt to extort payments.
- Locking hospitals out of their critical system will delay the swift medical response required during these unprecedented times and it could also directly lead to deaths.
- The ransomware appears to be spreading primarily via e-mails, often falsely claiming to contain information or advice regarding the coronavirus from a government agency, which encourages the recipient to click on an infected link or attachment.
- Prevention and Mitigation efforts are crucial to stopping the attacks.
- Interpol continues to stand by its member countries and provide any assistance necessary to ensure vital healthcare systems remain untouched and the criminals targeting them held accountable.
- Interpol also issued a Purple Notice to seek or provide information on modus operandi, objects, devices and concealment methods used by criminals.
Changed Pattern of Crimes:
- Interpol warned that with a majority of people working from home due to the pandemic, there was a change in the pattern of crimes.
- Following is the change
- Fraudulent trade in personal protective equipment and anti-viral medicines,
- Individuals/businesses on reduced income becoming potential targets of loan sharks (Persons who loan money at extremely high interest rates and often use threats of violence to collect debts).
- The lockdown period has made business establishments/factories vulnerable to thefts.
- Since more people were at home, the number of burglaries had dropped. But thieves are increasingly targeting factories or business premises that were locked.
- Domestic violence cases have risen since the start of coronavirus-related quarantines, with reports showing women and children at greater risk of abuse.
- Recent weeks have seen increased online activity by paedophiles (persons who are sexually attracted to children) seeking child sexual abuse material.
- This is being intensified by a shortage of moderators who identify and remove offensive material from networks.
Steps Taken by the Government:
- Alerts received by the Government of India on the threat of ransomware/malware attacks have been communicated to the concerned departments.
- Institutions and individuals have been appealed not to open any mail or link on coronavirus data or home remedies unless it is from a trusted source like a government agency.
- They were also cautioned about a possibility of e-mail spoofing, where a suspect operating from a remote location would send a mail that would appear as if it came from a known person.
NATIONAL MISSION ON INTERDISCIPLINARY CYBER PHYSICAL SYSTEMS (NMICPS)
12, Mar 2020
Why in News?
- Recently, the Indian Institute of Technology (IIT) Ropar, Punjab is setting up a Sectoral Application Hub in Technologies for Agriculture and Water.
About National Mission on Interdisciplinary Cyber Physical Systems (NMICPS):
- The hub is being set up under the National Mission on Interdisciplinary Cyber Physical Systems (NMICPS) and is granted by Union Government’s Science and Engineering Research Board.
- It will bring solutions for stubble management, water quality improvement and mapping of hazardous substances in water.
- It aims at carrying out translational research and work with concerned departments to develop prototypes, products and implementations.
- It was launched in 2018 and is implemented by the Department of Science & Technology for a period of five years.
- It covers entire India which includes Central Ministries, State Governments, Industry and Academia.
Its objectives are:
- It is a comprehensive mission which would address technology development, application development, human resource development & skill enhancement, entrepreneurship and start-up development in Cyber-Physical System (CPS) and associated technologies.
- The mission aims at establishing 15 Technology Innovation Hubs (TIH), six Application Innovation Hubs (AIH) and four Technology Translation Research Parks (TTRP).
- They have four focused areas namely:
- Technology Development.
- HRD & Skill Development.
- Innovation, Entrepreneurship & Start-ups Ecosystem Development.
- International Collaborations.
Cyber-Physical Systems:
- These systems integrate sensing, computation, control and networking into physical objects and infrastructure, connecting them to the Internet and to each other.
Few Potential Applications:
- Driverless cars that communicate securely with each other on smart roads.
- Sensors in the home to detect changing health conditions.
- Improving agricultural practices.
- Enabling scientists to address issues arising out of climate change.
- Advances in cyber-physical systems will enable capability, adaptability, scalability, resiliency, safety, security and usability that will far exceed the simple embedded systems of today
GLOBAL MEDICAL DATA LEAKAGE
05, Feb 2020

Why in News?
- Greenbone Sustainable Resilience, a German cyber security firm has recently published it report on Global Medical Data Leak.
About the News:
- The report stated that medical details of over 120 million Indian patients have been leaked and made freely available on the Internet.
- The report also places Maharashtra at the top of the States affected by the global medical data leak followed by Karnataka.
- The report classifies countries in the “good”, “bad” and“ugly” categories based on the action taken by their governments in stopping it.
- India ranks second in the “ugly” category, after the U.S.
- The data leak of records includes images of CT scans, X-rays, MRIs and even pictures of the Patients.
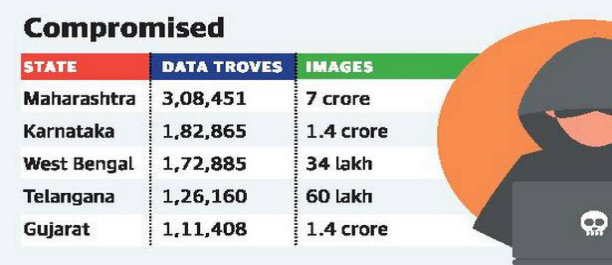
What is the Concern?
- The leak is worrying because the affected patients can include anyone from the common working man to politicians and celebrities.
- In image-driven fields like politics or entertainment, knowledge about certain ailments faced by people from these fields could deal a huge blow to their image.
- The other concern is of fake identities being created using the details, which can be misused in any possible number of ways.
What is the cause for Leakage?
- The leak was facilitated by the fact that the Picture Archiving and Communications Systems (PACS) servers, where these details are stored, are not secure and linked to the public Internetwithout any protection, making them easily accessible to malicious elements.
Way Forward:
- PACS Servers should be secured properly and should not be connected to public internet to avoid such kind of leakages.
- Since these medical datas leakages lead to anti-social activities such as organ donation scandals, the particular medical institution should be held accountable for the datas.
- Any communication between a doctor and a patient is a privileged one. A doctor or a hospital is thus ethically, legally and morally bound to Maintain Confidentiality.
QUANTUM COMPUTING
26, Nov 2019
Why in News?
- Recently quantum processor of Google solved a problem in just 3 minutes.
About:
- It describes the point where quantum computers can do things that classical computers cannot.
- Google had achieved Quantum Supremacy by solving a problem which even with the most powerful classical computer available today would take about 10,000 years to solve in just 3 minutes.
Significances:
- Help to discover exotic materials for variety of requirements.
- Provide fool proof cryptographic protection against online frauds.
- Enable drug discovery to fight diseases.
- Design efficient batteries.
- Smarter devices and gadgets.
Qubit/Quantum Bit
- It is the basic unit of quantum information.
- It is a two-state quantum mechanical system, one of the simplest quantum systems displaying the peculiarity of quantum mechanics.
- In a classical system, a bit would have to be in one state or the other.
- Quantum mechanics allows the qubit to be in a coherent superposition of both states simultaneously, a property which is fundamental to quantum mechanics and quantum computing.
- The power of the quantum computer comes from its inherent parallelism, the ability to manipulate a large collection of qubits in one shot in ways that a classical computer will not be able to match up.
‘WHATSAPP DID NOT INFORM GOVT. OF SYSTEM BREACH’
04, Nov 2019

Why in News?
- WhatsApp has stated that some Indian users of WhatsApp came under surveillance using an Israeli spyware.
Highlights:
- WhatsApp in October 2019 sued the NSO Group, an Israeli surveillance firm and developers of Pegasus, which is reportedly behind the technology that helped unnamed entities hack into roughly 1,400 devices across at least 20 countries, including India, Bahrain, Mexico and UAE. Indian users were among those impacted by the spyware.
- The NSO Group is an Israeli technology firm, which claims on its website that its products are used “exclusively” by government intelligence and law enforcement agencies “to fight crime and terror”.
Concerns:
- WhatsApp has over 1.5 billion users globally, of which India alone accounts for about 400 million.
- The vulnerability of the users to such spying is of grave concern with regard to breach of their privacy.
- Government has stated that WhatsApp failed to inform the government of a breach of its system despite being legally bound to do so under Section 70(B) of the IT Act. They are legally bound to inform (computer emergency response team) CERT or any other relevant government agencies about the details of such attacks on Indian citizens.
- Despite WhatsApp arguing that they had given information to CERT-IN, the government has stated that it was a communication in pure technical jargon without any mention of Pegasus or the extent of breach.
- Thus the information shared was only about a technical vulnerability but nothing on the fact that privacy of Indian users had been compromised. Lack of clarity on this issue shows the loopholes in the current processes.
- The government has been blamed for trying to use the spyware to target specific people. However the government has stated that government agencies operate strictly as per provisions of law and a well-established protocol for interception.
- Government has claimed that reports of breach of privacy of Indian citizens on WhatsApp were attempts to malign the government and are completely misleading. The episode has taken up a political tone.
PRIVACY RIGHTS & WRONGS
12, Oct 2019

Why in News?
- TRAI had commenced a process of consultations to bring over the top (OTT) services like WhatsApp and Telegram under “lawful interception”.
Objectives:
- The objective of the exercise is public security since criminals and terrorists are known to use end-to-end encryption offered by such services to fly under the radar.
- Parity has always been an issue since telecom providers complain that they are regulated and must respond to requests for information from governments and agencies. But the OTT sector is untrammelled.
Is Interception Technologically Feasible, at all?
- Technology companies have argued that end-to-end encryption is completely private between the correspondents in the conversation.It is encrypted by a pair of security keys which their devices exchange, and which are available to no one else, not even the OTT provider. Providers are unable to provide governments with any communications content, except metadata like the frequency of contact.
- The US Attorney General’s, along with his counterparts in Australia and the UK, has requested Mark Zuckerberg not to deploy systems that preclude any form of access to content, even for preventing or investigating the most serious crimes.
Need for Such Technologies:
- Concerns about crime, terrorism and lethal mischief-making using encrypted communications are legitimate.
- Worldwide, the pressure is developing on providers and platforms to make content available for inspection.
Against privacy:
- Privacy concerns are equally legitimate because compromising security would degrade privacy across platforms.Blackberry had kept a copy of encrypted communications and provided it to the governments of India, Saudi Arabia, and the United Arab Emirates. Now, it is an inconsequential player. Privacy is now recognised as a right. It would open the door to situations like the NSA mass surveillance scandal.
CYBER CRIME COORDINATION CENTRE
19, Jul 2019

Why in News?
- The Central Government has rolled out a scheme for establishment of Indian Cyber Crime Coordination Centre to handle issues related to cybercrime in the country in a comprehensive and coordinated manner.
- Central Government has taken steps to spread awareness about cybercrimes to prevent such crimes and to speed up investigation.
Initiatives:
- Establishment of National Critical Information Infrastructure Protection Centre (NCIIPC) for protection of critical information infrastructure in the country.
- All organizations providing digital services have been mandated to report cyber security incidents to CERT-In expeditiously.
- Cyber Swachhta Kendra (Botnet Cleaning and Malware Analysis Centre) has been launched for providing detection of malicious programmes and free tools to remove such programmes. Issue of alerts and advisories regarding cyber threats and counter-measures by CERT-In. Issue of guidelines for Chief Information Security Officers (CISOs) regarding their key roles and responsibilities for securing applications / infrastructure and compliance. Provision for audit of the government websites and applications prior to their hosting, and thereafter at regular intervals.
- Formulation of Crisis Management Plan for countering cyber-attacks and cyber terrorism.
- Empanelment of security auditing organisations to support and audit implementation of Information Security Best Practices. Conducting cyber security mock drills and exercises regularly to enable assessment of cyber security posture and preparedness of organizations in Government and critical sectors.
- Conducting regular training programmes for network / system administrators and Chief Information Security Officers (CISOs) of Government and critical sector organisations regarding securing the IT infrastructure and mitigating cyber-attacks.
CHINESE-BUILT DRONES MAY STEAL DATA, WARNS U.S.
22, May 2019

Why in News:
- Washington has warned that Chinese-made drones could be giving spy agencies in Beijing
- “unfettered access” to stolen data.
Details;
- The U.S. government has “strong concerns about any technology product that takes American data into the territory of an authoritarian State that permits its intelligence services to have unfettered access to that data or otherwise abuses that access,”
- The warning comes as China’s tech sector attracts unprecedented scrutiny amid China-US trade war. Washington has cranked up the heat on China’s Huawei by banning American companies from selling or transferring U.S. technology to the telecom’s giant. U.S. intelligence believes Huawei is backed by the
- Chinese military and that its equipment could provide Beijing’s spy agencies with a
- backdoor into the communications networks of other countries.
India and drones:
- The National Drones Policy drafted by the Ministry of Civil Aviation came into effect
- With the policy coming into effect, flying drones or remotely-piloted aircraft have become legal in India.
- Also, the Ministry of Civil Aviation has kick-started the online registration of drones in India through its Digital Sky portal.
Highlights of the policy
- Under the new policy, Nano drones which weigh less than 250 grams or equal does not need a registration or license.
- Digital Sky portal – It is an online platform as part of an enforcement system designated as No Permission No Take-off (NPNT).
- It includes procedures to conduct a drone operation, including final flight permission immediately before the operation.
- Permission – Following registration, DGCA will issue a Unique Identification Number (UIN) or Unmanned Aircraft Operator’s Permit (UAOP)
- Zones – Flying in the ‘green zones will require only intimation of the time and location of the flights via the portal or the app.
- But permissions will be required for flying in ‘yellow zones’, and flights will not be allowed
- in the ‘red zones.
GOVERNMENT DEVELOPS ONLINE GAME TO COUNTER CYBER CRIMES AGAINST CHILDREN
14, Sep 2018

- The government has launched its own game application for children in a bid to counter incidents of cyber-crimes against children due to dangerous games like ‘blue whale’ and ‘momo’ challenges.
Background:
- Known as the ‘cyber trivia’ app, it would include a set of multiple-choice questions which will help the kids learn ways to deal with strangers on the internet, the National Commission for Protection of Child Rights (NCPCR) said.
- It is an attempt to teach these children in a fun way, what should be done if they are contacted by a stranger on the Internet who might ask for their pictures or ask them to do things
- The game has been developed amid rising cases of suicide by children due to challenges like ‘blue whale’ and ‘momo’. It will soon be available on online stores.
- The children these days outsmart even their parents. They do not understand the dangers the cyber world poses and online games would be really effective. That is the reason we decided to develop this game
- A child psychologist, said that the app is based on behaviour modification technique. “We use a system of rewards and punishments to encourage positive behaviour and discourage negative behaviour. It is a standard technique of behaviour modification therapy”. She said the game might interest younger children but to capture the interest of teenagers it needs to evolve.
National Commission for Protection of Child Rights (NCPCR):
- The National Commission for Protection of Child Rights (NCPCR) emphasizes the principle of universality and inviolability of child rights and recognizes the tone of urgency in all the child related policies of the country.
- For the Commission, protection of all children in the 0 to 18 years age group is of equal importance. Thus, policies define priority actions for the most vulnerable children. This includes focus on regions that are backward or on communities or children under certain circumstances, and so on.
- The NCPCR believes that while in addressing only some children, there could be a fallacy of exclusion of many vulnerable children who may not fall under the defined or targeted categories.
Data localisation
29, Aug 2018

Why in news?
- S. technology giants plan to intensify lobbying efforts against stringent Indian data localisation requirements, which they say will undermine their growth ambitions in India.
What is data localisation?
- Data localization is the act of storing data on any device that is physically present within the borders of a specific country where the data was generated.
Advantages of data localisation:
- The main advantages of securing citizen’s data, data privacy, data sovereignty, national security, and economic development of the country.
- It acts as a solution for the advent of cloud computing that raises important questions on accountability of service providers who store Indian users’ data outside of the country’s boundaries, leading to a conflict of jurisdiction in case of any dispute.
- Also, minimal or deregulated governance on critical data, due to absence of localisation requirements, could be detrimental to India’s national security as data would be outside the purview of existing data protection legislation. This shall be avoided in in case of data localisation.
- In addition to these, India also aspires to become a global hub for, among others, cloud computing, data hosting and international data centres, all of which are prompting the government to enact data localisation requirements for accelerating the nation’s economic growth, especially in the sphere of digital technologies.
Centre wants supreme court to get tough with FB, YouTube
28, Aug 2018

- The efforts by Internet giants to curb circulation of online videos of sexual violence against women and children inadequate, the government is likely to seek “stricter directions” to service providers, such as Facebook and YouTube, from the Supreme Court.
Directions sought:
- Reducing the time taken by the intermediary to comply with content removal requests under certain Sections of the IT Act to less than 10 hours from about 36 hours at present.
- The service providers be asked to employ agencies for identification and removal of sexually violent content, particularly videos relating to child pornography and rape.
- Intermediaries should be asked to keep a complete trail of forwarding of unlawful content and verify and maintain identifiers of the users that can help attribute information to the users.
- The centre also wants service providers to be able to identify the origin of such content.
Lynching: Social Media sites to be held responsible
16, Aug 2018

Why in news?
- A panel headed by Union Home Secretary Rajiv Gauba, which deliberated on measures to check incidents of lynching, submitted its report to a Group of Ministers headed by Home Minister Rajnath Singh.
- In May and June, more than 20 people were lynched based on fake posts or rumours floating on various social media platforms.
- The panel discussed such incidents and is learnt to have come to the conclusion that social media platforms needed to act in a “time-bound” manner.
Panel Members:
- The panel report will first be discussed by the GoM, whose members are External Affairs Minister Sushma Swaraj, Transport Minister Nitin Gadkari, Law Minister Ravi Shankar Prasad and Social Justice and Empowerment Minister Thawar Chand Gehlot.
Background:
- According to the sources, the panel is learnt to have suggested that the existing provisions in the Indian Penal Code (IPC) and criminal procedure code (CrPC) should be tightened by inserting new clauses.
- Social media platforms — Facebook, WhatsApp, YouTube and Twitter — would be made accountable for not blocking malicious posts and videos when brought to their notice and an “FIR could be lodged against their country heads” for not complying with government orders and they could be prosecuted under law.
- The committee of secretaries held consultations with a cross-section of society and other stakeholders before submitting its report to the Group of Ministers.
- They suggested that some countries employ non-governmental organisations and volunteers who proactively surf the Internet.
- They have created a portal where people can report such videos and content and that can be forwarded by the National Crime Records Bureau [the nodal body] to the States concerned for appropriate action
- The Centre asked to appoint an officer in each district at the level of Superintendent of Police, set up a special task force to gather intelligence, and closely monitor social media contents to prevent mob attacks on people on the suspicion of being child-lifters or cattle smugglers.






